
What is Nessus? Nessus is a remote security scanning tool, which scans computer and identifies vulnerabilities by scanning the system registry, files, ports, missing patches, misconfigurations, and software flaws. Nessus plugins uses the common vulnerabilities and Exposures architecture for easy cross-linking. New exploits are being identified every day so it is important to monitor and scan systems daily so vulnerabilities can be identified and remediated. While Nessus is a subscription-based vulnerability scanner you could download Nessus Essentials for free and follow along with the lab below. Nessus Essentials doesn’t expire and can scan up to 16 IPs.
What is a Plugin? Tenable writes plugins in using the Nessus proprietary scripting language called Nessus Attack Scripting Language (NASL). The Plugins will contain vulnerability information, remediation recommendation or
actions. The script will test for the presence of security issues. The plugin can be associated with the Common Vulnerability Scoring System (CVSS) v2 and v3 simultaneously to help calculate the determining Risk Factors. Once a vulnerability becomes public Nessus will go about pushing a plug-in to identify the vulnerability. It is important for customers to ensure they receive plug-in updates/feeds daily to stay current with the latest vulnerabilities. Each plug in has a Plugin ID for the detected vulnerability. Paid Nessus subscriptions like the Security Center can provide Plugin Details and the source NASL code(Not all plugins provide NASL).
reference
https://docs.tenable.com/nessus/Content/AboutNessusPlugins.htm

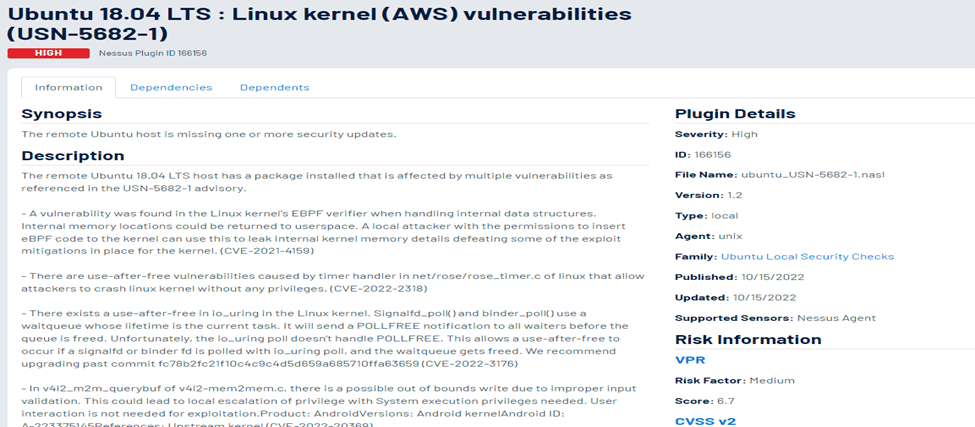
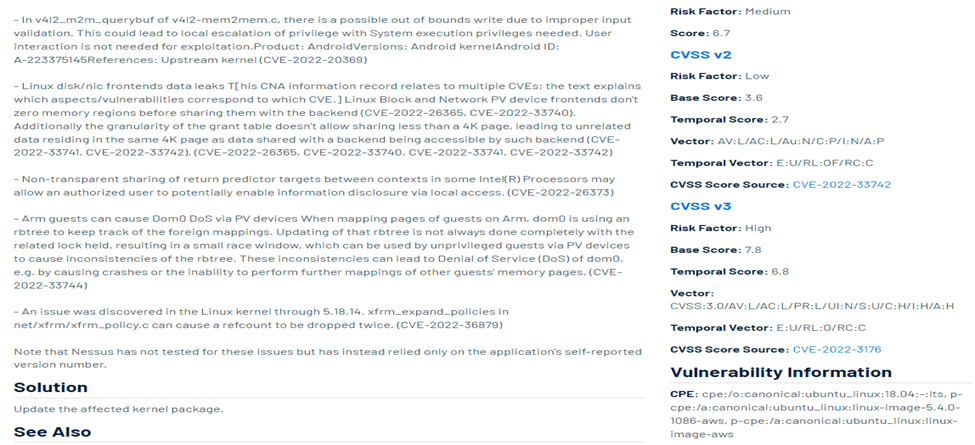
Credentialed Scan vs Non credentialed Scan
Nessus allows you the ability to provide credentials so it could provide more insight into the system vulnerabilities. The credentials supplied to Nessus are used to authenticate and scan files with special permissions. When credentials are not provided to Nessus the scan is considered to be non-credentialed. If possible, it is best to conduct a credentialed scan so to identify more vulnerabilities.

What is vulnerability management?
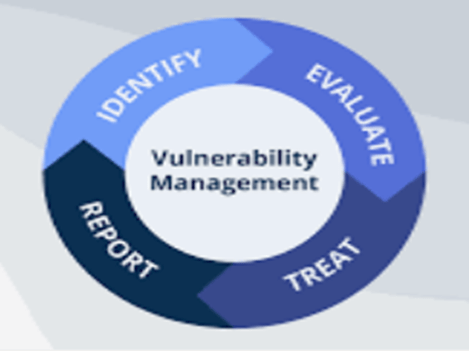
Vulnerability management is the process of identifying, evaluating, treating, and reporting on security vulnerabilities in a system. Automation and scanning could assist with identifying vulnerabilities and prioritizing them. Vulnerability management could be broken down into 4 steps.
- Identifying Vulnerabilities through scanning or correlating system information
- Evaluating Vulnerabilities through determining the risk, impact, and scope
- Treating Vulnerabilities through Remediation, Mitigation, or Acceptance
- Reporting Vulnerabilities through vulnerability assessments
What is ACAS? Assured Compliance Assessment Solution (ACAS) vulnerability scanning is the mandated enterprise vulnerability scanning capability for network and components that are owned or operated by the DoD. Per TASKORD 20-0020 DoD operated systems should use Tenable.sc security center, Nessus Vulnerability Scanner, Nessus Agents, and Nessus Network Monitoring. Commands are subject to CCRI inspections, so it is imperative to implement ACAS suite of tools and have an effective vulnerability management process. This ACAS solution allows for centralized management of consolidated data. This data can be used for data visualization, dashboards, and reporting compliance.

Please see the project below where I demonstrate how to perform a Nessus scan against a Windows 2012 in a Lab environment. Once the scan is complete, I go about remediating the system. Later, I utilize these scan results to demonstrate how the vulnerability scan can be utilized to
You could Download Nessus Essentials

I hope you enjoy this introductory to Nessus, ACAS, and Plugins.
Leave a comment